RtPOS
RTPOS is a ram scraper used to find credit card data within a process memory address space. Credit card data is saved into a log file that needs to be manually grabbed by the malware operators.
Sample:
Filename: alohae.exe
SHA256: fb749c32b58fd1238f21d48ba1deb60e6fb4546f3a74e211f80a3ed005f9e046
It supports two command-line options to either install itself as a service or remove the existing installation:
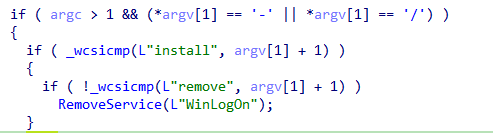
When executed with the install argument, RTPOS installs itself as a service named WinLogon with the start type set to auto start:
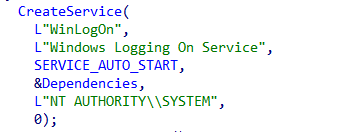
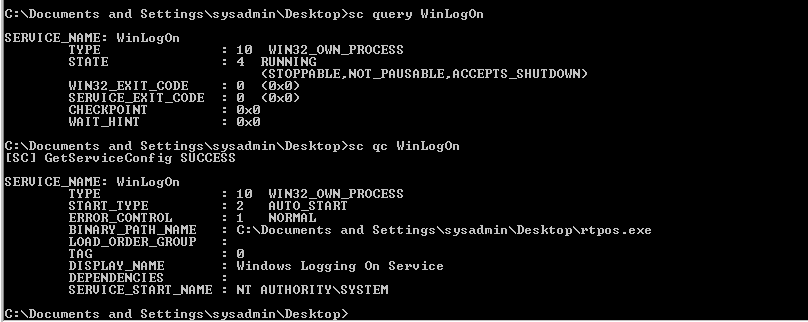
Service details:
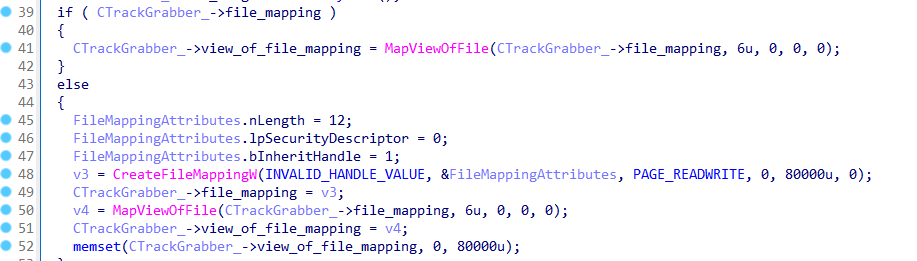
RTPOS creates a file mapping to store the credit card data before saving it to disk:
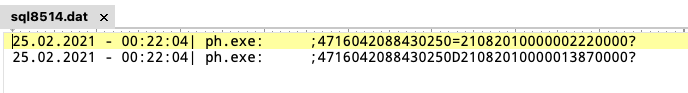
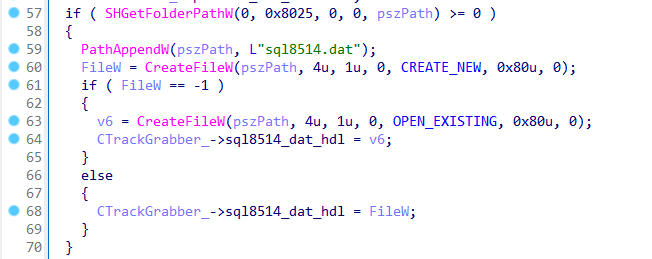
RTPOS saves the logs with credit card data in a file named sql8514.dat inside the folder C:\Windows\System32 or C:\Windows\SysWOW64\ if the malware runs in a 64-bit machine:
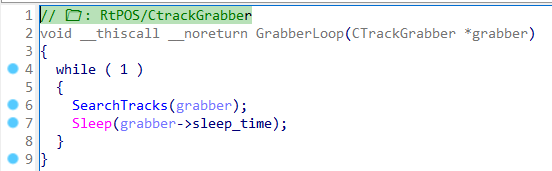
The malware enters in a loop where it will keep scanning the running processes for credit card data:
To read the memory of the targeted processes, RTPOS uses the classic combinations of Windows APIS:
- CreateToolhelp32Snapshot
- Process32FirstW/Process32NextW
- OpenProcess
- VirtualQueryEx
- ReadProcessMemory
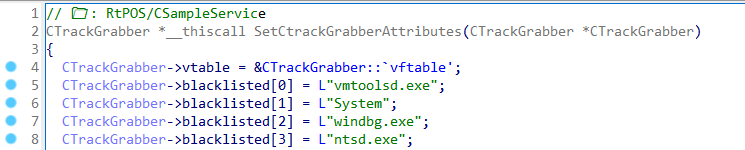
It will avoid scanning vmtoolsd.exe, System, windbg.exe, and ntsd.exe processes:
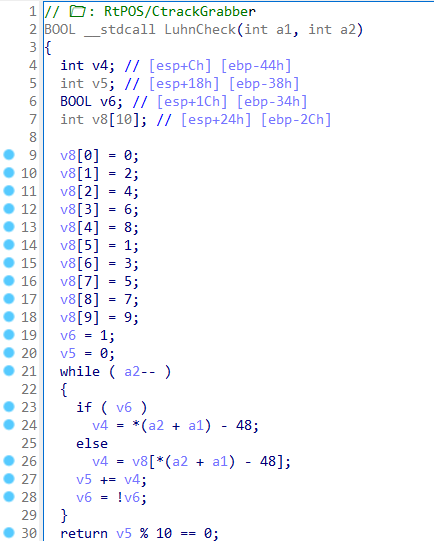
The credit card tracks are validated with the Luhn algorithm:
Example of the content of sql8514.dat: